As today’s organizations are well aware, determined threat actors and advanced persistent threats (APTs) can be patient and resourceful in their efforts to evade your defenses. When they finally are successful in gaining access to systems and networks, standard security solutions often “fail silently,” unable to detect an intrusion, let alone alert you.
A major culprit in this failure is often a lack of visibility. Endpoint detection and response (EDR) is the most promising solution for addressing this challenge. This article offers insight into what EDR is, how it works and why it should be a key component of a comprehensive security strategy.
Definition of Endpoint Detection and Response
An answer to the question, “What is endpoint detection and response?,” should start by acknowledging that at its core, EDR has one of the most critical security capabilities there is: visibility.
However, to define EDR products more completely at a basic level, it’s important to understand that endpoint detection and response solutions record system activities and events taking place on endpoints and provide security teams with the visibility they need to uncover incidents that would otherwise remain invisible.
Learning what is EDR and choosing the right solution means navigating a range of vendor offerings that can vary greatly in scope and efficacy.
This article is intended to further your understanding of endpoint detection and response by explaining where endpoint detection and response fits in a robust security strategy. Ultimately, it aims to show you the benefits of incorporating endpoint detection and response into your security approach.
What is the difference between EDR and Antivirus? Antivirus is the prevention component of endpoint security, which aims to stop threats from entering a network. When threats slip past an antivirus, EDR detects that activity and allows teams to contain the adversary before they can move laterally in the network.
What are the Key Aspects of EDR Security?
According to Gartner, effective EDR must include the following capabilities:
- Incident data search and investigation
- Alert triage or suspicious activity validation
- Suspicious activity detection
- Threat hunting or data exploration
- Stopping malicious activity
What to look for in an EDR Solution
Understanding the key aspects of EDR and why they are important will help you better discern what to look for in a solution. It’s important to find EDR software that can provide the highest level of protection while requiring the least amount of effort and investment — adding value to your security team without draining resources. Here are the six key aspects of EDR you should look for:
1. Visibility:
Real-time visibility across all your endpoints allows you to view adversary activities, even as they attempt to breach your environment, and stop them immediately.
2. Threat Database:
Effective EDR requires massive amounts of telemetry collected from endpoints and enriched with context so it can be mined for signs of attack with a variety of analytic techniques.
3. Behavioral Protection:
Relying solely on signature-based methods or indicators of compromise (IOCs) lead to the “silent failure” that allows data breaches to occur. Effective endpoint detection and response requires behavioral approaches that search for indicators of attack (IOAs), so you are alerted of suspicious activities before a compromise can occur.
4. Insight and Intelligence:
An endpoint detection and response solution that integrates threat intelligence can provide context, including details on the attributed adversary that is attacking you or other information about the attack.
5. Fast Response:
EDR that enables a fast and accurate response to incidents can stop an attack before it becomes a breach and allow your organization to get back to business quickly.
6. Cloud-based Solution:
Having a cloud-based endpoint detection and response solution is the only way to ensure zero impact on endpoints, while making sure capabilities such as search, analysis and investigation can be done accurately and in real time.
Watch our on-demand webcast to understand the role of EDR as part of an overall endpoint protection strategy: “Endpoint Detection and Response (EDR): Choosing the right solution”
How Does EDR Work?
Answering the question, “How does endpoint detection and response work?” should focus on finding an ideal solution that includes the required functionality, but also provides unique features that can provide greater protection against today’s most sophisticated adversaries.
The CrowdStrike® Falcon® solution, Falcon Insight™ EDR provides next-gen capabilities that surpass conventional defenses, which leave you open to silent failure and can allow attackers to dwell in your environment for days, weeks or even months without raising an alarm. The solution lies in having continuous and comprehensive real-time visibility into what is happening on your endpoints and the ability to apply behavioral analysis and actionable intelligence to stop an incident from turning into a breach.
CrowdStrike Falcon Insight provides the following critical capabilities:
Automatically Uncovers Stealthy Attackers
Falcon Insight pairs comprehensive visibility across all endpoints with IOAs and applies behavioral analytics that analyze billions of events in real time to automatically detect traces of suspicious behavior.

CrowdStrike Falcon EDR dashboard displaying detected threats
Understanding individual events as part of a broader sequence allows the Falcon Insight agent to apply security logic derived from CrowdStrike Intelligence. If a sequence of events matches a known IOA, the Falcon agent will identify the activity as malicious and automatically send a detection alert. Users can also write their own custom searches, going back up to 90 days, with Falcon Insight’s cloud architecture returning query results in five seconds or less.
Integrates With Threat Intelligence
Integration with CrowdStrike’s cyber threat intelligence provides faster detection of the activities and tactics, techniques and procedures (TTPs) identified as malicious. This delivers contextualized information that includes attribution where relevant, providing details on the adversary and any other information known about the attack.
Security Operation Centers (SOCs) and security analysts receive a detailed narrative that specifies the “who, why and what” of the event — empowering organizations to be better prepared to protect itself.
Managed Threat Hunting for Proactive Defense
As part of the Falcon platform, Falcon OverWatch™ managed threat hunting service adds an extra level of protection with a team of expert hunters, acting on the customer’s behalf, to ensure threats don’t get missed and ultimately, to prevent a mega breach.
Using Falcon Insight EDR, the OverWatch team members work proactively to hunt, investigate and advise on threat activity in your environment. When they find a threat, they work alongside your team to triage, investigate and remediate the incident, before it has the chance to become a full-blown breach.
Provides Real-Time and Historical Visibility
Falcon Insight acts like a DVR on the endpoint, recording relevant activity to catch incidents that evaded prevention. Customers are given comprehensive visibility into everything that is happening on their endpoints from a security perspective as the Falcon agent tracks hundreds of different security-related events, such as process creation, drivers loading, registry modifications, disk access, memory access or network connections.
This gives security teams the useful information they need, including:
- local and external addresses to which the host is connected
- all the user accounts that have logged in, both directly and remotely
- a summary of changes to ASP keys, executables and administrative tool usage
- process executions
- both summary and detailed process-level network activity, including DNS requests, connections, and open ports
- archive file creation, including RAR and ZIPS
- removable media usage
This complete oversight of security-related endpoint activity allows security teams to “shoulder surf” an adversary’s activities in real time, observing which commands they are running and what techniques they are using, even as they try to breach or move around an environment.
Accelerates Investigations
CrowdStrike endpoint detection and response is able to accelerate the speed of investigation and ultimately, remediation, because the information gathered from your endpoints is stored in the CrowdStrike cloud via the Falcon platform, with architecture based on a situational model.
The model keeps track of all the relationships and contacts between each endpoint event using a massive, powerful graph database, which provides details and context rapidly and at scale, for both historical and real-time data. This enables security teams to quickly investigate incidents.
This speed and level of visibility, combined with integrated, contextualized intelligence provides the information needed to thoroughly understand the data. This enables security teams to effectively track even the most sophisticated attacks and promptly uncover incidents, as well as triage, validate and prioritize them, leading to faster and more precise remediation.
Enables Fast and Decisive Remediation
Falcon Insight can isolate the endpoint, which is called “network containment.“ It allows organizations to take swift and instantaneous action by isolating potentially compromised hosts from all network activity.
When an endpoint is under containment, it can still send and receive information from the CrowdStrike cloud, but it will remain contained even if the connection to the cloud is severed and will persist with this state of containment during reboots.
When it comes to responding to emerging threats, time is of the essence and responders need visibility in depth and in real time, so they can remediate with speed and decisiveness.
Falcon Insight includes Real Time Response, which provides the enhanced visibility that enables security teams to immediately understand the threats they are dealing with and remediate them directly, while creating zero impact on performance.
Real Time Response includes two sets of built-in commands you can execute during investigations to accelerate remediation.
Information collectors allow security teams to immediately understand the risk and scope of a threat by enabling tasks such as:
- Explore the file system and extract files
- List running processes
- Extract Windows event log
- Query Windows registry
- List current network connections and configuration
- Extract process memory
- Calculate file hashes
- Collect environment variables
- Collect additional desired information using PowerShell or other tools
Remediation actions enable teams to take action to contain or remediate a threat with speed and decisiveness including:
- Delete a file
- Kill a process
- Delete or modify Windows registry key or value
- Put a file
- Run a script or an executable file
- Encrypt a file
- Restart/Shutdown
With CrowdStrike’s cloud-native architecture, lightweight agent and unified console, Real Time Response capabilities can be delivered to any system anywhere in the world with zero impact on cost or performance.
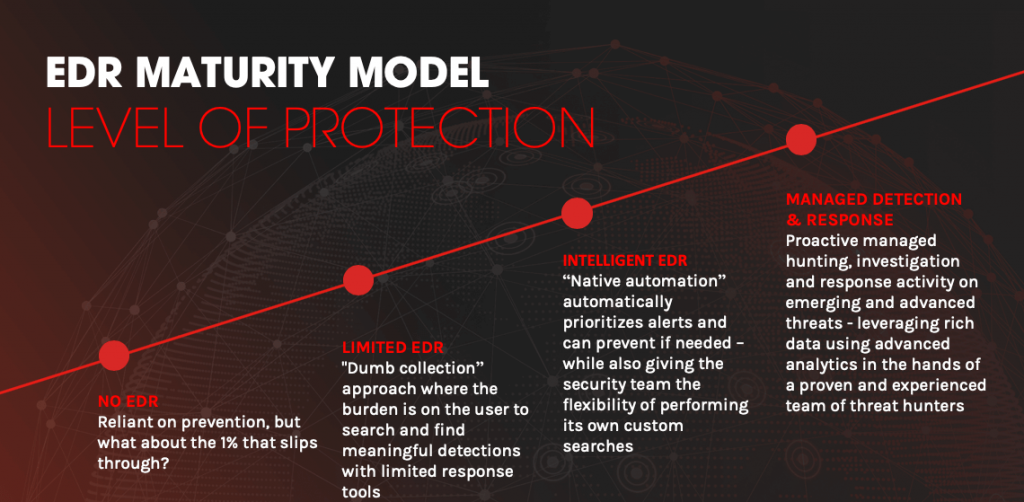
Download our white paper on how the “EDR maturity model” can help you choose the solution that best meets your organization’s needs: “Endpoint Detection and Response (EDR): Automatic protection against advanced threats”
Why is EDR Important?
All organizations should know by now that with enough motivation, time and resources, adversaries will eventually devise a way to get through your defenses, no matter how advanced. The following are some compelling reasons EDR should be a part of your endpoint security strategy.
Reason #1: Prevention alone can’t ensure 100 percent protection
When prevention fails, your organization can be left in the dark by its current endpoint security solution. Attackers take advantage of this situation to linger and navigate inside your network.
Reason #2: Adversaries can be inside your network for weeks and return at will
Because of silent failure, attackers are free to move around in your environment, often creating back doors that allow them to return at will. In most cases, the organization learns about the breach from a third party, such as law enforcement or its own customers or suppliers.
Reason #3: Organizations lack the visibility needed to effectively monitor endpoints
When a breach is finally discovered, the victim organization can spend months trying to remediate the incident because it lacks the visibility required to see and understand exactly what happened, how it happened and how to fix it — only to see the attacker return within a matter of days.
Reason #4: Access to actionable intelligence is needed to respond to an incident
Organizations may not only lack the visibility required to understand what is happening on its endpoints, it may not be able to record what is relevant to security, store it and then recall the information quickly enough when needed.
Reason #5: Having the data is only part of the solution
Even when data is available, security teams need the resources required to analyze and take full advantage of it. This is why many security teams find that soon after they’ve deployed an event collection product, such as a SIEM, they are often facing a complex data problem. Challenges around knowing what to look for, speed, and scalability begin cropping up and other problems surface before their primary objectives can even be addressed.
Reason #6: Remediation can be protracted and costly
Without the capabilities listed above, organizations can spend weeks trying to discern what actions to take — often the only recourse is to reimage machines, which can disrupt business processes, degrade productivity and ultimately cause serious financial loss.
Want to see an EDR solution in action? Click the button below to watch an on-demand demo of the CrowdStrike endpoint protection platform.


