Ransomware Definition

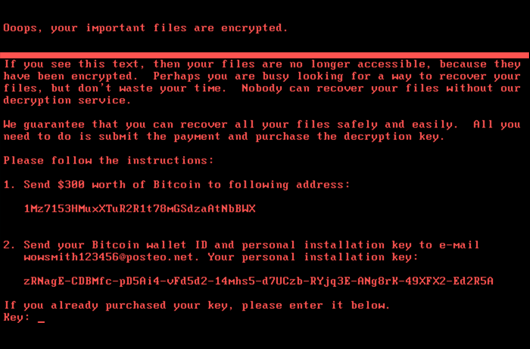
Ransomware is a type of malware that encrypts access to your system or personal files and demands a payment (ransom) to get your files back — often within a certain period of time and sometimes for an increasing amount after a missed deadline (or more than one).
Payment may be required through cryptocurrency, credit card or untraceable gift cards — and paying doesn’t ensure that you regain access. Even worse, victims who do pay are frequently targeted again. And just one infection can spread ransomware throughout an entire organization, crippling operations. It’s maddening, panic-inducing — and effective.
With ransoms ranging from hundreds of dollars to tens of thousands, cybercriminals have extracted billions from victims across all industries in recent years. In fact, Cybersecurity Venture predicts that ransomware damage will exceed $11 billion in 2019. One reason it’s so effective is that it takes many guises, and you have to be aware of all of them in order to effectively protect your data and your entire network.
Download this white paper to get an in-depth analysis of the history of ransomware and learn how adversary TTPs are evolving to maximize profits: A Deep Dive into Ransomware’s Evolution
How Does Ransomware Infect Your Computer?
There are several ways ransomware can get into your computer or system. One of the most common is via email phishing and spam — messages that include either a malicious attachment or a link to a malicious or compromised website. Once an unsuspecting user opens the attachment or clicks the link, the ransomware can infect the victim’s computer and spread throughout the network.
Another route is using an exploit kit to take advantage of a security hole in a system or program, like the infamous WannaCry worm that infected hundreds of thousands of systems worldwide using a Microsoft exploit. It can also take the form of a fake software update, prompting users to enable admin capabilities and install malicious code.
Once ransomware has infected the system, it generally either blocks access to the hard drive or encrypts some or all of the files on the computer. You may be able to remove the malware and restore your system to a previous state, but your files will remain encrypted because they’ve already been made unreadable, and decryption is mathematically impossible without the attacker’s key.
The ransom itself is set at a level that’s low enough to be payable, but high enough to make it worthwhile for the attacker, prompting companies to do a cost-benefit analysis of how much they’re willing to pay to unlock their systems and resume daily operations. Cyber criminals may also target certain organizations or industries to exploit their specific vulnerabilities and maximize the chances of a ransom being paid.
Universities, for example, often have smaller security teams and a large user base that engages in a lot of file sharing, so defenses are more easily penetrated. Medical organizations may also be targeted because they often need immediate access to their data and lives may be at stake, leading them to pay right away. And financial institutions and law firms may be more likely to pay the ransom because of the sensitivity of their data—and to pay it quietly to avoid negative publicity.
See real-world examples of ransomware in action, the sophisticated tactics being used by a variety of advanced persistent threats (APTs), and what you can do to detect them: Detecting the most complex “file-less” ransomware exploits
What Are the Different Types of Ransomware?
Ransomware takes many forms, but they all have one thing in common — they demand a ransom in exchange for restored access to your system or files. It’s also important to remember that you’re dealing with criminals, they don’t always follow through with their end of the “deal.” Ransomware attacks are designed to prey on people’s desperation and fear in order to convince victims to pay.
Here are the most common types:
1. Crypto malware or encryptors are one of the most well-known and damaging variants. This type encrypts the files and data within a system, making the content inaccessible without a decryption key.
2. Lockers completely lock you out of your system, so your files and applications are inaccessible. A lock screen displays the ransom demand, possibly with a countdown clock to increase urgency and drive victims to act.
3. Scareware is fake software that claims to have detected a virus or other issue on your computer and directs you to pay to resolve the problem. Some types of scareware lock the computer, while others simply flood the screen with pop-up alerts without actually damaging files.
4. Doxware or leakware threatens to distribute sensitive personal or company information online, and many people panic and pay the ransom to prevent private data from falling into the wrong hands or entering the public domain. One variation is police-themed ransomware, which claims to be law enforcement and warns that illegal online activity has been detected, but jail time can be avoided by paying a fine.
5. RaaS (Ransomware as a Service) refers to malware hosted anonymously by a “professional” hacker that handles all aspects of the attack, from distributing ransomware to collecting payments and restoring access, in return for a cut of the loot.
How to Avoid & Prevent Ransomware
Once ransomware encryption has taken place, it’s often too late to recover that data. That’s why the best defense relies on proactive prevention. Robust backup is, of course, a foundational best practice to prepare in case of an attack, but newer malware variants can also delete or damage backups.
Discover which ransomware defense approaches are the most effective by downloading our detailed white paper on: RANSOMWARE DEFENSE: THE DO’S AND DON’TS
Ransomware is constantly evolving, making protection a challenge for many organizations. Follow these best practices to help keep your operations secure:
1. Train all employees on cybersecurity best practices:
Your employees are on the front line of your security. Make sure they follow good hygiene practices — such as using strong password protection, connecting only to secure wifi and being on constant lookout for phishing — on all of their devices.
2. Keep your operating system and other software patched and up to date:
Hackers are constantly looking for holes and backdoors to exploit. By vigilantly updating your systems, you’ll minimize your exposure to known vulnerabilities.
3. Use software that can prevent unknown threats:
While traditional antivirus solutions may prevent known ransomware, they fail at detecting unknown malware threats. The CrowdStrike Falcon® platform provides next-gen antivirus (NGAV) against known and unknown malware using AI-powered machine learning. Rather than attempting to detect known malware iterations, Falcon looks for indicators of attack (IOAs) to stop ransomware before it can execute and inflict damage.
4. Continuously monitor your environment for malicious activity and IOAs:
CrowdStrike® Falcon Insight™ endpoint detection and response (EDR) acts like a surveillance camera across all endpoints, capturing raw events for automatic detection of malicious activity not identified by prevention methods and providing visibility for proactive threat hunting.
For stealthy, hidden attacks that may not immediately trigger automated alerts, CrowdStrike offers Falcon OverWatch™ managed threat hunting, which comprises an elite team of experienced hunters who proactively search for threats on your behalf 24/7.
5. Integrate threat intelligence into your security strategy:
Monitor your systems in real time and keep up with the latest threat intelligence to detect an attack quickly, understand how best to respond, and prevent it from spreading. CrowdStrike Falcon® Intelligence automates threat analysis and incident investigation to examine all threats and proactively deploy countermeasures within minutes.
Ransomware Examples
Below are just a few examples of some infamous ransomware detected over the last few years:
NotPetya
NotPetya was first detected in 2017 rapidly infiltrating systems across multiple countries. What’s particularly nasty about this family of ransomware is its use of stealthy propagation techniques that allow it to swiftly move laterally to encrypt other systems across an organization. NotPetya ransom notes have demanded $300 USD for each infected machine. For a deep dive on this family of ransomware, check out our in-depth technical analysis on Notpetya or watch our Notpetya postmortem webcast.
SamSam
Developed and operated by the cyber adversary, BOSS SPIDER, SamSam has been observed using unpatched server-side software to enter an environment. Most notably, SamSam was behind the 2018 ransomware attack on the city of Atlanta, Georgia. The attack left 8,000 city employees without their computers, and citizens were unable to pay their parking water bills and parking tickets. To read more about the SamSam attack on Atlanta, Georgia, visit our blog post on the lessons learned from SamSam.
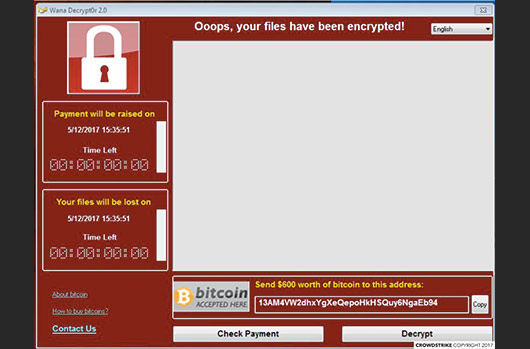
WannaCry
Also referred to as WCry, WanaCrypt, or Wanna, WannaCry was identified in May 2017 during a mass campaign affecting organizations across the globe. WannaCry has targeted healthcare organizations and utility companies using a Microsoft Windows exploit called EternalBlue, which allowed for the sharing of files, thus opening a door for the ransomware to spread. To learn more about how an attack unfolds, check out our technical analysis of WannaCry.
Watch the video below to learn how CrowdStrike Stops WannaCry Ransomware:
What’s the Next Step?
CrowdStrike is a leader in next-generation endpoint security, threat intelligence and incident response. CrowdStrike’s core technology, the CrowdStrike Falcon platform, stops breaches by preventing and responding to all attack types.
To find out more about how CrowdStrike prevents ransomware, click the button below: